OS-Specific Security Issues
Operating Systems and their Security Issues
Router Security
See my page on the risks of backdoors for problems intentionally inserted into network gear.
See the Router Security site for router bugs, checklists, tests, and more. It is aimed at technically adept users of SOHO routers, it isn't about rack-mount enterprise routers.
Here are some great references on current best practices for Cisco router configurations:
Secure IOS Template Secure BGP Template Cisco recommended OSPF configuration
SCADA, Industrial Control
ICS-CERTUS-CERT includes ICS-CERT or the Industrial Control Systems Cyber Emergency Response Team.
This category of network-connected industrial control systems was attacked by the Stuxnet advanced persistent threat.
See the French government's Classification Method and Key Measures for how to do this right. That's their ANSSI ICS industrial systems cybersecurity standard document.
Modern automobiles have perhaps 50 to 200 small single-board computers. Microsoft and QNX initially dominated the field, with Windows Embedded and proprietary QNX systems. But Linux has been rapidly growing with the support of the Automative Grade Linux Work Group, the nonprofit Genivi, open source initiatives like OpenXC, webinos, Tizen, and others. Unfortunately, must of the "Internet of Things" is based on Linux of rather old releases with no way to update or patch them.
This Car Runs
on Code
Many Cars Have a Hundred
Million Lines of Code
The Next Big OS War
is in Your Dashboard
In 2018 researchers reported multiple ways of hacking BMW cars, including some remote attacks. BMW's response summarizes to "Only smart hackers could do that, and it would be wrong, so no one should worry about this."
Trend Micro on
CAN standard
shortcoming
More details on
CAN standard
shortcoming
A 2009 IEEE Spectrum article started by saying that the U.S. Air Force F-22 has about 1.7 million lines of code, the F-35 has about 5.7 million lines, and Boeing's 787 Dreamliner has about 6.5 million lines. But a premium class automobile of 2009 "probably contains close to 100 million lines of software code." MIT Technology Review wrote about this in late 2012, as did Wired.
However, the article The Fallacy Behind Counting Lines of Code points out that total software content is a poor measurement. The software is bloated, so that one code base can support any permutation of available options, many of them never offered to consumers. Much of is non-critical, and none is subject to the standards of aviation, so there is much less testing. Consider the common estimates of 15 to 50 defects per 1,000 lines of code, multiplied by automotive software bloat.
Engine Controllers
There are large searchable databases of the keys and other bits needed to unlock "warez", pirated copies of Cisco certification exams, etc., at Crack Spider and CrackWay.
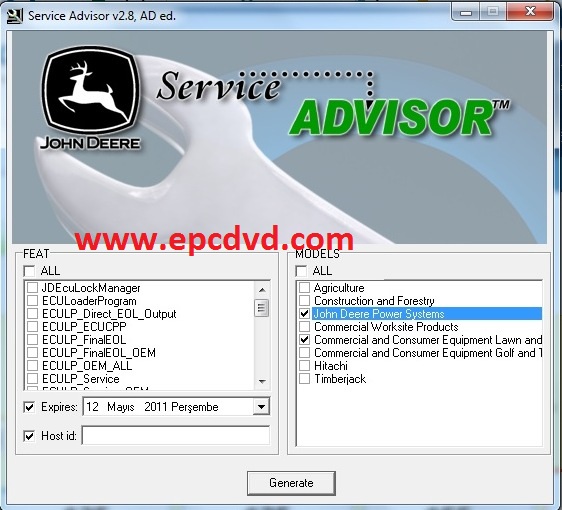
This category includes license key generators for embedded engine control systems for large trucks, construction equipment, and generator sets. The illicit license key generators are sold online by operations like EPC Software.
You can see in the below that the seller uses Turkish, which isn't the dominant language at John Deere headquarters. "12 Mayıs 2011 Perşembe" means "Thursday, 12 May 2011".
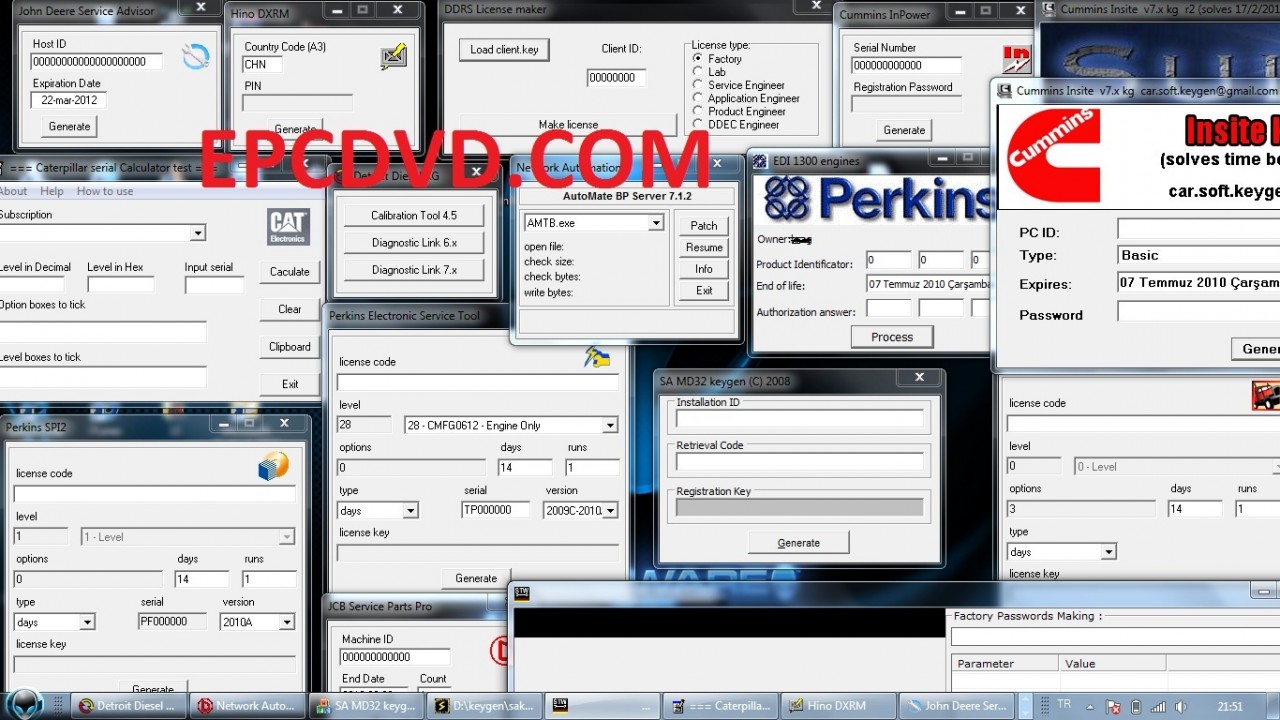
Of course, many of these are scams. They either take your money and give you nothing, or they've sold you a link to download something that doesn't do what it promises, or something that's infested with malware. The epcsoftware.com operation used to be epcdvd.com, and has also operated as tukkor.com and several other URLs, according to this forum of angry people calling it out as an illegal scam. The second page of that thread lists several other URLs where heavy equipment keygens (and malware masquerading as such) is sold.
Vicearticle
A Vice article, "Why American Farmers Are Hacking Their Tractors With Ukrainian Firmware", publicized this trend. Equipment manufacturers lock out the owners. The owners turn to Ukrainian on-line dealers. Both the manufacturers and the owners are deeply invested in a "Real America" image.
Wiredarticle
Wired later had an article "They Hacked McDonald’s Ice Cream Machines—and Started a Cold War" about a small company that dared to provide fixes for McDonald's notoriously faulty soft-serve machines, and how big business set out to destroy them.
Automatic Teller Machine (ATM) / Cash Machine Security
The ATM Marketplace site has a "buyer's guide" that lets you compare features, and in some cases it reveals some details of network interface, CPU, and even OS.
ATM attacksTrend Micro has a fascinating paper on ATM hardware and software attacks. Most attacks are physical, but criminal gangs are starting to attack across compromised bank networks. The majority of bank machines world-wide use Windows XP or Windows XP Embedded. Older machines run Windows NT, Windows CE, or Windows 2000.
In the U.S., machines physically attached to a bank or credit union must have configurations specified by the Office of the Comptroller of the Currency. Other ATMs (in stores, bars and restaurants, sports venues) do not. Freestanding ATMs may have a bank's name on them, but they are not subject to the same security requirements.
Specific attacks include:
Skimer-A:
"Credit card skimming malware targeting ATMs",
Sophos Naked Security
"More details on the Diebold ATM Trojan horse case",
Sophos Naked Security
"New ATM malware captures PINS and Cash — Updated"
Wired
Ploutus:
"Backdoor.Ploutus Reloaded — Ploutus Leaves Mexico",
Symantec
"Texting ATMs for Cash Shows Cybercriminals Increasing Sophistication",
Symantec
Padpin / Tyupkin:
"Bakdoor.Padpin", Symantec
"NCR ATM API Documentation Available on Baidu",
F-Secure
"Tyupkin: manipulating ATM machines with malware",
Kaspersky Lab
"Can the ATM industry stop Tyupkin in its tracks?",
ATM Marketplace
GreenDispenser:
"Meet GreenDispenser: A New Breed of ATM Malware",
Proofpoint
Alice:
"Alice: A Lightweight, Compact, No-Nonsense ATM Malware",
Trend Micro TrendLabs
ATM Card Skimmers
All AboutSkimmers
See Brian Kreb's All About Skimmers series.
Also see this SensePost article on deep-insert skimmers.
Fuel Pump Credit Card Skimmers
How gas pump credit card skimmers work Skimmer ScannerShort version: There are only a few master keys to open fuel pump cabinets. It takes about 30 seconds to open the cabinet, unplug a cable, insert a small PC board and short cable, and close the cabinet. The small board reads and stores the cleartext serial data coming from the credit card reader. The criminal returns later and retrives that data over Bluetooth. For more details see this Sparkfun tutorial.
The Skimmer Scanner smart phone app lets you scan a pump for the distinctive Bluetooth identity, telling you that you shouldn't use that pump as it probably has a skimmer installed.
IoT or "Internet of Things"
This collection of IoT documents is from Bruce Schneier's Crypto-Gram, Feb 15 2017:
"IoT Security and Privacy Recommendations", IoT Broadband Internet Technical Advisory Group, Nov 2016 "IoT Security Guidance," OWASP, May 2016 "Strategic Principles for Securing the Internet of Things (IoT)," US Department of Homeland Security, Nov 2016 "Security," OneM2M Technical Specification, Aug 2016 "Security Solutions," OneM2M Technical Specification, Aug 2016 "IoT Security Guidelines Overview Document," GSM Alliance, Feb 2016 "IoT Security Guidelines For Service Ecosystems," GSM Alliance, Feb 2016 "IoT Security Guidelines for Endpoint Ecosystems," GSM Alliance, Feb 2016 "IoT Security Guidelines for Network Operators," GSM Alliance, Feb 2016 "Establishing Principles for Internet of Things Security," IoT Security Foundation, undated "IoT Design Manifesto," www.iotmanifesto.com, May 2015 "NYC Guidelines for the Internet of Things," City of New York "IoT Security Compliance Framework," IoT Security Foundation, 2016 "Principles, Practices and a Prescription for Responsible IoT and Embedded Systems Development," IoTIAP, Nov 2016 "IoT Trust Framework," Online Trust Alliance, Jan 2017 "Five Star Automotive Cyber Safety Framework," Feb 2015 "Hippocratic Oath for Connected Medical Devices," Jan 2016 "Industrial Internet of Things Volume G4: Security Framework," Industrial Internet Consortium, 2016 "Future-proofing the Connected World: 13 Steps to Developing Secure IoT Products," Cloud Security Alliance, 2016 "Comments of EPIC to the FTC on the Privacy and Security Implications of the Internet of Things," Electronic Privacy Information Center, Jun 2013 "Internet of Things Software Update Workshop (IoTSU)," Internet Architecture Board, Jun 2016 "Multistakeholder Process; Internet of Things (IoT) Security Upgradability and Patching," National Telecommunications & Information Administration, Jan 2017 "We All Live in the Computer Now," The Netgain Partnership, Oct 2016
Bluetooth Low Energy or BLE is being built into an increasing number of devices, with all sorts of privacy and other security issues. Including, ah, recreational endoscopes and other sex toys.
Ars Technica article BLE scanning Penetration testing
Linux
My Pages
Linux DoD/DISA STIG Compliance
How to harden a default Linux or OpenBSD installation
Also see:
STONIX — Los Alamos National Laboratory — a program for hardening UNIX and Linux
Of historical interest:
UNIX IP Stack Tuning Guide
Securing and optimizing Linux
Libsafe protects against buffer overflow and "stack smashing" Saint Jude Linux Kernel Module
Hardening Solaris user authentication
If you have Solaris 8 or earlier, you are stuck with the mid-1970's "classic UNIX" authentication. Only the first 8 password characters matter, and they're hashed in a way that was fairly secure against brute-force attack by, oh, common computers of the mid-1970's...
If you have Solaris 10 or later, it uses much more secure password hashing by default. Arbitrarily long pass phrases, hashed with MD5.
If, on the other hand, you have Solaris 9,
while it is capable of the stronger method, you have
to specify it.
First, modify /etc/default/passwd and change
the line now reading:
PASSLENGTH=6
to a more ambitious number.
Edit /etc/security/policy.conf, first verifying
that it contains this line:
CRYPT_ALGORITHMS_ALLOW=1,2a,md5
Now un-comment this line by removing the leading "#":
CRYPT_ALGORITHMS_DEPRECATE=__UNIX__
Change the default hashing algorithm like this:
CRYPT_DEFAULT=1
Once you've done that, you will need to re-set the passwords
with passwd to put the hashes into the more
secure form.
The algorithms are as follows, note that the "1/2a/md5" notation was taken from Cisco:
-
1— BSD and Linux (GNU) style MD5 hashing. This is probably the best for interoperability, and should be quite strong. -
2a— OpenBSD style hashing, using a 1024-round lossy variation of Blowfish as a one-way operation. It has a password length limit, see the manual pages forcrypt.conf,crypt_bsdmd5, andcrypt_bsdbf. -
md5— Some Solaris-specific MD5 hashing.
ULTRIX/ OSF/1 / Digital Unix / Tru64 Unix Security
HP-UX Security
IRIX Security
macOS Security
Hardening guides for macOS:
ERNW Hardening OS X
This series of papers describes the firmware and the
hardening of both the GUI and command-line interface:
Securing macOS X
macOS 10.3 (Panther)
macOS 10.4 (Tiger)
macOS 10.5 (Leopard)
DOS Security
AS/400 Security
Novell Security
VMS Security
Think you're secure because you run VMS? See the first chapter of UNDERGROUND — Tales of Hacking, madness and obsession on the Electronic Frontier (ISBN 1-86330-595-5)
Mainframe Security
Windows Security
Cleaning and Optimizing a Windows Computer Windows Security from the Ground UpWindows security is way better than it used to be, but some issues remain. Remember that "NT" is Microsoft's term for an entire family of operating systems. It refers to all forms of Windows with user authentication, so NT 3.x and NT 4.x back in the 1990s through the Windows 20** Server series and Windows 10. Windows 98 was the last one that wasn't NT.
Three crucial components seem to be far more intertwined
in Windows than in other operating systems:
• The operating system,
• The graphical interface, and
• The environment of user's processes.
The lack of separation imposes limits on how secure it can be.
See, for example, the
Microsoft Security Servicing Criteria for Windows,
which clearly states that there is no intent to provide
a security boundary between the kernel and
Administrative users and processes.
Microsoft Security Servicing Criteria for Windows
The accepted method for administering the system is
to login to the graphical interface as
Administrator or a user in the
Administrators group
and use graphical tools.
There is next to no separation of privileges.
Compare that to the UNIX model where the operating system
and the graphical interface are relatively separate, and
where cautious administrators log in as unpriviliged users.
Only to the extent absolutely necessary do they elevate
privileges, using su or
Role-Based Access Control (RBAC) tools.
Then there are the other really bad design decisions — the window message queueing API, really questionable TCP/IP design decisions (like file and print sharing over IP broadcast), etc.
EMET, ProcessMitigations, and Windows Defender Exploit Guard
EMET ProcessMitigationsmodule Windows Defender
Exploit Guard
Enhanced Mitigation Experience Toolkit or EMET has been a free toolkit for Windows security. You can download it from Microsoft.
The ProcessMitigations module, also called the Process Mitigation Management Tool, has replaced EMET.
Windows Defender Exploit Guard protects Windows 10 (version 1709 and later) and Windows Server 2016.
Vendors Installing Malware
Vendors may install malware on Windows systems,
leaving it pretty much impossible for customers
to secure their systems.
For example,
HP shipped laptops with a keylogger in the
audio driver.
News report
Vulnerability disclosure
Issues with Windows file system insecurity
The Windows NT family supports EFS, Encrypting File System, which looks like a good design, at least at first:
- Every file is encrypted using a symmetric cipher and a key randomly generated when the file was created.
- The collection of keys is stored in a file encrypted with a key based on the user's password.
- You type your password to login, and so your login session has access to the key store.
- If you change your password while logged in, your old (current) password is used to decrypt the key store and then the new (future) password is used to encrypt the key store.
- The remaining problem is that if you use EFS and you reset a users's password, you lose the ability to decrypt that key store and thus all of that user's files are lost as undecipherable ciphertext.
- The good news (in this very specific case) is that Windows password security is so weak that you can use something like Rainbow Tables to break the user's password in minutes instead of resetting it and losing the data.
The disturbing part is
this disclosure
on one of Microsoft's pages:
Windows NT zero-fills memory and zeroes
the sectors on disk where a file is placed
before it presents either type of resource
to an application.
owever, object reuse does not dictate that
the space that a file occupies before
it is deleted be zeroed.
This is because Windows NT/2K is designed
with the assumption that the operating system
controls access to system resources.
However, when the operating system is not
active it is possible to use raw disk editors
and recovery tools to view and recover data
that the operating system has deallocated.
Even when you encrypt files with Win2K's
Encrypting File System (EFS), a file's original
unencrypted file data is left on the disk
after a new encrypted version of the file
is created.
You can always break in with bootable media, such as the Windows "rescue" boot media, a.k.a. the NT break-in media or the NT password and registry editor media. Or, you could simply use bootable Linux media. Non-Windows boot media would let you directly access the block storage devices and recover the unencrypted copies.
Historical Problems with Windows
Jim Allchin was a vice-president and later co-president of Microsoft. He retired from Microsoft as of 30 January 2007, the day on which Microsoft officially released their Windows Vista operating system to consumers. Allchin was co-president of Microsoft's Platforms & Services Division, was the manager of the Vista project, and led the development of a number of Microsoft's operating systems. Allchin provides some interesting information:
"I am not sure how the company lost sight of what matters to our customers (both business and home) the most, but in my view we lost our way. think our teams lost sight of what bug-free means, what resilience means, what full scenarios mean, what security means, what performance means, how important current applications are, and really understanding what the most important problems [our] customers face are. I see lots of random features and some great vision, but that doesn't translate into great products. I would buy a Mac today if I was not working at Microsoft. ... Apple did not lose their way. ..."
It appears that the guy in charge of the Microsoft operating systems had very little confidence in them. The above is from the Allchin memo to Bill Gates and Steve Ballmer, January 2004, read more about the background here, here, and here.
Then there was the problem of privilege escalation through the Win32 API. Microsoft said that this was not fixable but not really a problem. While testifying before the U.S. Department of Justice in an anti-trust case, Allchin referred to this as a fundamentally unsecureable design representing a threat to U.S. national security due to the U.S. government's reliance on Windows. Allchin then mentioned the Windows message-queuing subsystem, which allows for what's known as the "Shatter" attack. Read more about it here, here, and here.
Commentary on leaked Windows source codeThis was at least partly fixed in Vista, but some issues remained.
After Microsoft said "Outsiders cannot be allowed to see the source code as that would damage US national security", they allowed the government of the People's Republic of China to view the source code. See, the PRC said they didn't want to buy Windows unless they could see the source code, and Microsoft didn't want to miss out on a big sale....
Then there are the three highly placed Microsoft executives whose internal communications were brought to light in a US District Court case, described in a New York Times article 9 March 2008. Their frustrations were caused by a lack of functionality and support in Vista, which at the time of their problems had been released as a supposedly finished product and was being sold for full retail price. The angry executives included:
- Jon A Shirley, a Microsoft board member, former president, and chief operating officer, "upgraded" two XP machines to Vista. Then he discovered that his printer, scanner, and film scanner all lacked Vista drivers. He had to go back to XP on one machine just to continue using those peripherals.
- Mike Nash, a Microsoft vice president who oversees Windows product management, bought a laptop with a "Windows Vista Capable" logo. That laptop lacked the needed graphics chip, could not run his favorite video-editing software, and could only run "a hobbled version of Vista". "I got burned", he said, "I now have a $2,100 e-mail machine."
- Steven Sinofsky, Microsoft's senior vice president responsible for Windows, heard about Jon Shirley's problems and said that drivers are missing in every category in Vista — "This is the same across the whole ecosystem."
This good multi-part discussion of Windows rootkits gets you into the technical details of how a rootkit works.
NIST has recommendations for securing Windows.
Fyodor maintained a collection of Windows exploits.
The classic John Kirch paper describes in detail why various Unix operating systems out-perform the Windows OS family.
For underlying philosophical problems leading to Windows security holes, see Byte, November 1997, pp 81-86 for details of how Microsoft re-invents broken wheels. Many problems that were discovered, and fixed, in other operating systems over the past few decades are routinely repeated by Microsoft! Also see Computers and Security, vol 17, no 2, pp 100-106 for details.
How Microsoft's poor (missing?) protection of the master cryptographic key exposes all of a user's net communication, "How to recover private keys for Microsoft Internet Explorer".
Comparing Windows to Linux and BSD
What is wrong with Linux?
It is as disorganized and resistant to organization as a herd of cats.
The kernel of the operating system itself is pretty good. But a Linux distribution is largely a pile of things that aren't the kernel and which tend to lower security:
- Application software — possibly buggy but relied on and assumed secure by users.
- Graphical environments — even worse! More likely to be buggy due to the volume of code, and just like Windows they hide details from users and automatically invoke programs in response to mouse events.
- Distribution installation and configuration tools — the installation process makes some security related assumptions on behalf of the administrator. The configuration tools used for ongoing administration may not be as bad, but they still make some assumptions that the administrator will not notice without great care.
What is wrong with BSD?
The same problems as Linux, just to far less degree.
While there are just three BSD implementations — FreeBSD, NetBSD, and OpenBSD, and their releases are far better controlled those for Linux, the BSDs use the same application software and graphical environment (GNU, KDE, Gnome, et al) as Linux. While their installation tools assume quite a bit of *NIX expertise (you may need to know how to set up a BSD partition/slice scheme by hand!), they may still hide some details from the installer.