
How NAT Works
NAT is Network Address Translation
You can very effectively protect your network from active attack with Network Address Translation or NAT. You assign your internal addresses from one or more of the reserved blocks defined in RFC 1918 — 10/8, 172.16/12, and 192.168/16. Those represent 16,277,216, 1,048,576, and 65,536 possible IPv4 addresses, respectively.
You then configure one or more border routers to do what's called IP masquerading, each hiding all the internal addresses behind one or more external IP addresses used by the exterior port of the router.
You can make all the connections you want from inside to out, but there is no way for a host on the outside to establish a connection to one of your inside hosts as those address blocks aren't routable out on the Internet.
Unless, of course, you go out of your way to set up static port forwarding, where some combination of IP address and TCP or UDP port on the exterior side of the NAT router is always mapped to some IP address and TCP or UDP port on the interior server.
How can you get away with telling lies?
1: Make certain that your lie is somewhat plausible.
2: Above all, make certain that you are consistent in your lying.
Network Address Translation (or IP masquerading) is a form of lying. It's something that firewalls, or routers in general, can do with the IP addresses in headers of packets they forward. The result is that details of the interior network are hidden, because the device doing NAT is effectively lying, masquerading as though it simultaneously is all of the hosts inside the networks it is hiding. To distant servers, your entire organization looks like one extremely busy host.
Using a NAT Firewall
Let's say that you have a cable modem or a DSL interface,
and you just connect your computer to the Internet.
This is dangerous if you're using Windows,
but a lot of people do this.
Your connection to the world might look something like this picture,
where modem
is your cable modem or DSL interface:
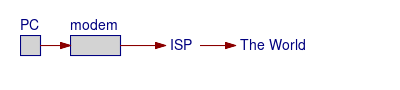
Well, that's how you see it from your house. Using my connection as an example, the reality is a bit more detailed. For an explanation of IP addresses, the slash notation, CIDR blocks and more, see my TCP/IP page.

Amazon
ASIN: B004XC6GJ0
Amazon
ASIN: B0100KRBA6
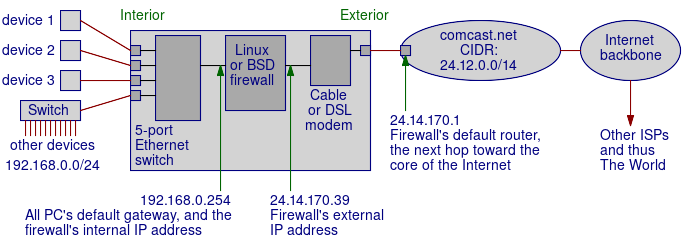
Now, if you find your PC's IP address details using my page of networking commands, we can add network addresses to the diagram, as seen below.
It is just one hop from my host to my default gateway,
which means, in network-speak, that we're adjacent.
Verify this with the following command, changing the IP address
to that of your default gateway:
traceroute 24.12.170.1
Or, if you're using Windows:
tracert 24.12.170.1
The important thing is that the modem isn't there
in terms of IP addresses.
While it does crucial things with signals,
it isn't really part of the networking topology
as far as networks and routing are concerned.

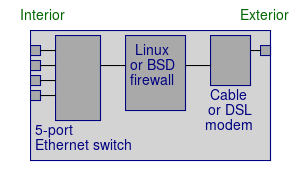
Now you go to the store and buy one of those "SOHO" (Small Office / Home Office) router/firewall boxes. They only cost about US$ 20-40. What's in the router? Quite a bit, actually. A typical router box really contains all this:

D-Link TM-G5240 802.11g wireless router, Cisco EZXS88W 8-port Ethernet switch, and MFJ-1278 multi-mode data controller. Small Internet access routers like this D-Link unit implement NAT.
On its exterior port, the firewall is a DHCP client, and acts just like your PC did to get an IP connection to the world.
Internally, the firewall does NAT and applies stateful packet filtering rules.
On its interior side, the firewall is a DHCP server for a private IP address space used inside your organization. RFC 1918 specifies a set of private blocks of IP addresses.
| Class | CIDR Block | IP Address Range |
| A | 10.0.0.0/8 |
10.0.0.0 - 10.255.255.255 |
| B | 172.16.0.0/12 |
172.16.0.0 - 172.31.255.255 |
| C | 192.168.0.0/16 |
192.168.0.0 - 192.168.255.255 |
So you plug your NAT firewall into where your PC used to go, and your PC into one of the firewall's Ethernet jacks. And other computers, and/or other Ethernet switches, into the other ports. So now you have something like the below:
Benefits
You could have up to 16,777,214 hosts on your
internal network,
if you used the 10.0.0.0/8 IP network.
But you only need one external IP address.
224 = 16,777,216
Minus two unusable addresses, hostid all 0's or all 1's:
224 - 2 = 16,777,214
No one outside can tell anything about your internal topology. You could have lots of routers and networks inside. From the outside it appears that you have only one very busy host, the exterior port of the NAT firewall.
Your internal addresses are not routable. The reserved RFC 1918 addresses are not routable. If an attacker managed to figure out your internal IP address, his packets would not go toward you but toward the core of the Internet. They would eventually hit a core router, one of the routers on the backbone. The core routers have no default routes, they have to know where everything is. And they don't have routes for 10/8, 172.16/12, or 192.168/16 — those networks effectively do not exist according to the routing tables of the public Internet.
Amazon
ASIN: B00JZWQW4C
Amazon
ASIN: B000BTL0OA
Multi-level NAT
You can do this in multiple levels. In the below diagram, a cable or FiOS or DSL router connects to the ISP's line. It gets a publicly routable external address, and this one is set up to use 192.168.0.0/24 on its internal side, both wired and wireless.
Then a second router, one with an Ethernet port as its external connection, is connected to one of the other router's port. This inner router must be configured to use a different block of IP addresses for its DHCP clients on its interior side.
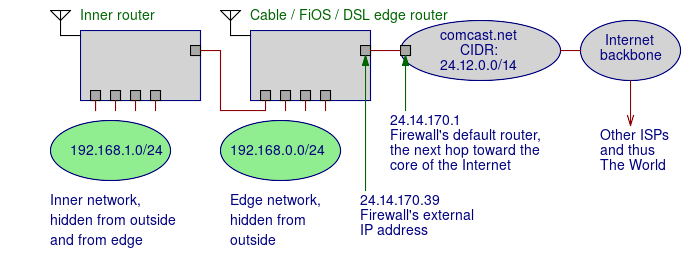
Let's say you connect a computer to that inner network, to one of the wired Ethernet ports or the wireless net of the inner router. That computer gets an address like 192.168.1.0, and it is told to route its packets through a gateway at 192.168.1.254, which is the inner router itself.
That inner router got an edge network address like 192.168.0.1 for its exterior (or "Internet" or "WAN") port, and it was told to route its packets through a gateway at 192.168.0.254, which is your edge router.
It, in turn, was told to use 24.14.170.39 for its exterior port, and route its packets through 24.14.170.1.
Now you can use traceroute (or, on Windows,
tracert) to test the path to Google:
$ traceroute www.google.com traceroute to www.google.com (172.217.0.4), 30 hops max, 60 byte packets 1 192.168.1.254 (192.168.1.254) 0.127 ms 0.078 ms 0.199 ms 2 192.168.0.254 (192.168.0.254) 0.254 ms 0.221 ms 0.307 ms 3 po102-rur01.lafayette.in.indiana.comcast.net (24.12.170.1) 8.002 ms 8.947 ms 14.140 ms 4 162.151.45.86 (162.151.45.86) 14.155 ms 14.344 ms 14.359 ms 6 be-22-ar01.indianapolis.in.indiana.comcast.net (68.86.188.97) 13.102 ms 14.215 ms 14.254 ms 5 be-3-ar01.area4.il.chicago.comcast.net (68.86.188.181) 20.629 ms 21.592 ms 22.703 ms [...]
You can do some interesting things with multi-level NAT, even in a home setting. Because both of your routers perform NAT, of course the outside world can't connect in. That is, unless you use video chat or another application that opens a static tunnel inbound through your edge router.
But now your inner router hides that inner network from your edge network. So...
Keep your systems on the inner network, let visitors use the edge network. That way they can use your Internet connection, but your computers are hidden behind NAT. Or...
Put the children's computers on the inner network, adults use the edge network. That makes access and monitoring much easier, and video chat apps on the inner network can only open a static tunnel from the edge network. And/or...
Put smart home devices on the inner network, and your computers on the edge network. Again, that protects poorly designed IoT (or Internet of Things) systems that you can neither patch nor configure to not open access to the outside world. If they open a static tunnel to expose themselves through the inner router, you can access them but the world can't.
If You're Using Wi-Fi With Multi-Level NAT
First, if you're doing that because your primary router only covers part of the home with Wi-Fi signals and you plan to run an Ethernet cable upstairs or to the other end of the house, first do a survey of your Wi-Fi signals.
Maybe your Wi-Fi router is on the ground floor, and your next-door neighbor's is upstairs, and you happen to be using the same channel. When you go upstairs, or your neighbor goes downstairs, each of finds that the desired signals are overwhelmed by those coming from next door. Without, of course, realizing that's what's going on.
Then, if you are going to have two Wi-Fi access points, you will want to put them on different channels so they don't interfere with either other.
For the 2.4 GHz bands, so 802.11b and 802.11b, the channels are 22 MHz wide and spaced every 5 MHz, so there's a lot of overlap. There are really just three useful channels: 1, 6, and 11.
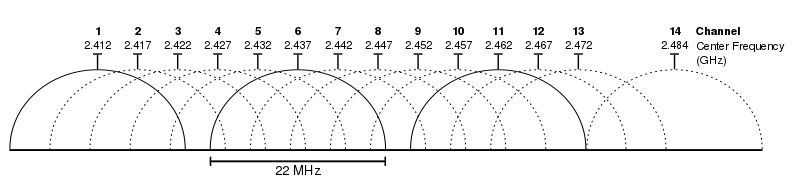
If the neighbors are far away and the band is fairly clear, channel 6 will probably give you the best performance. This is because embedded antennas involve many compromises, and probably give their best performance in the middle of the band.
Otherwise, use something like a smartphone app, or the Wi-Fi finder in your laptop's graphical desktop, or the command line if you dare:
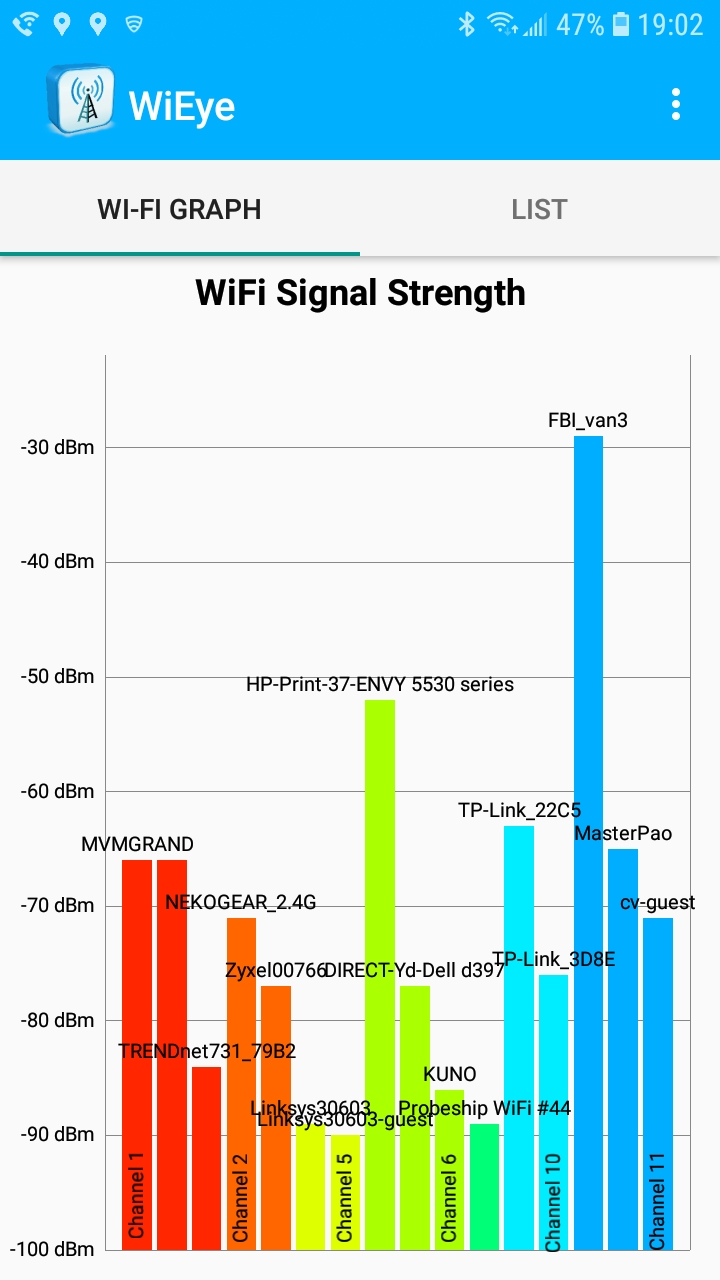
Here is the display of the WiEye app:
And, the
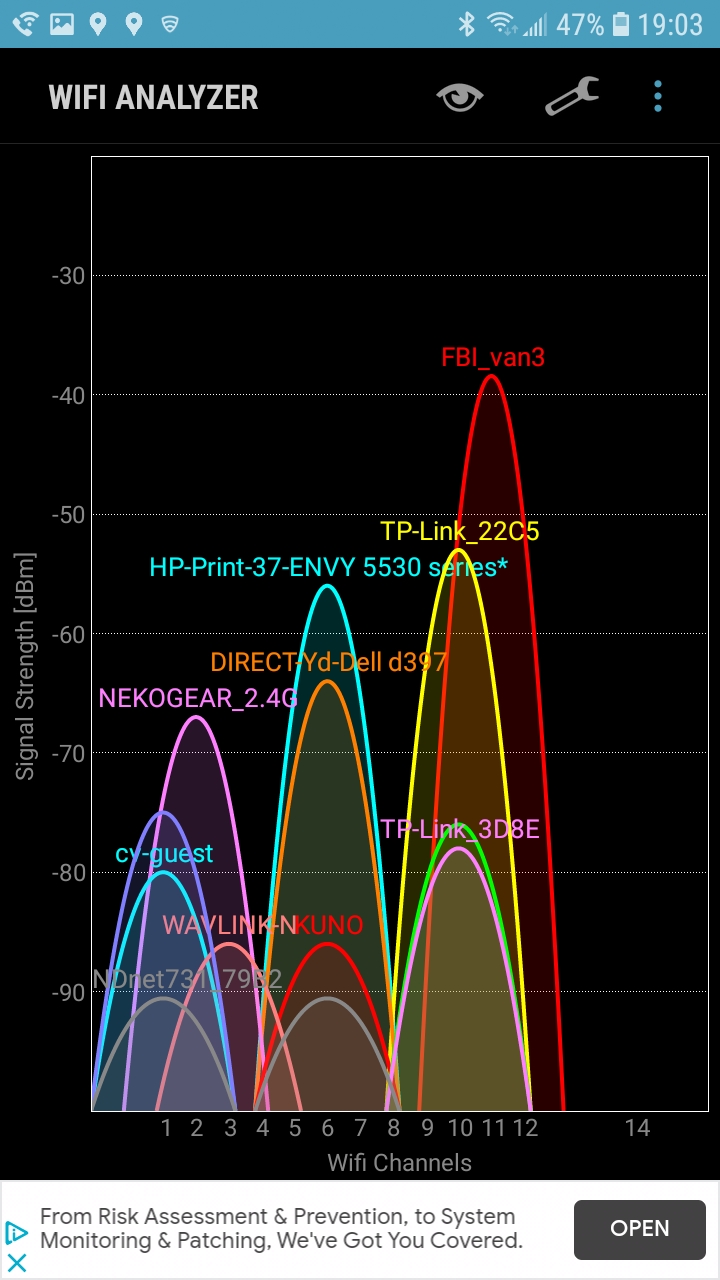
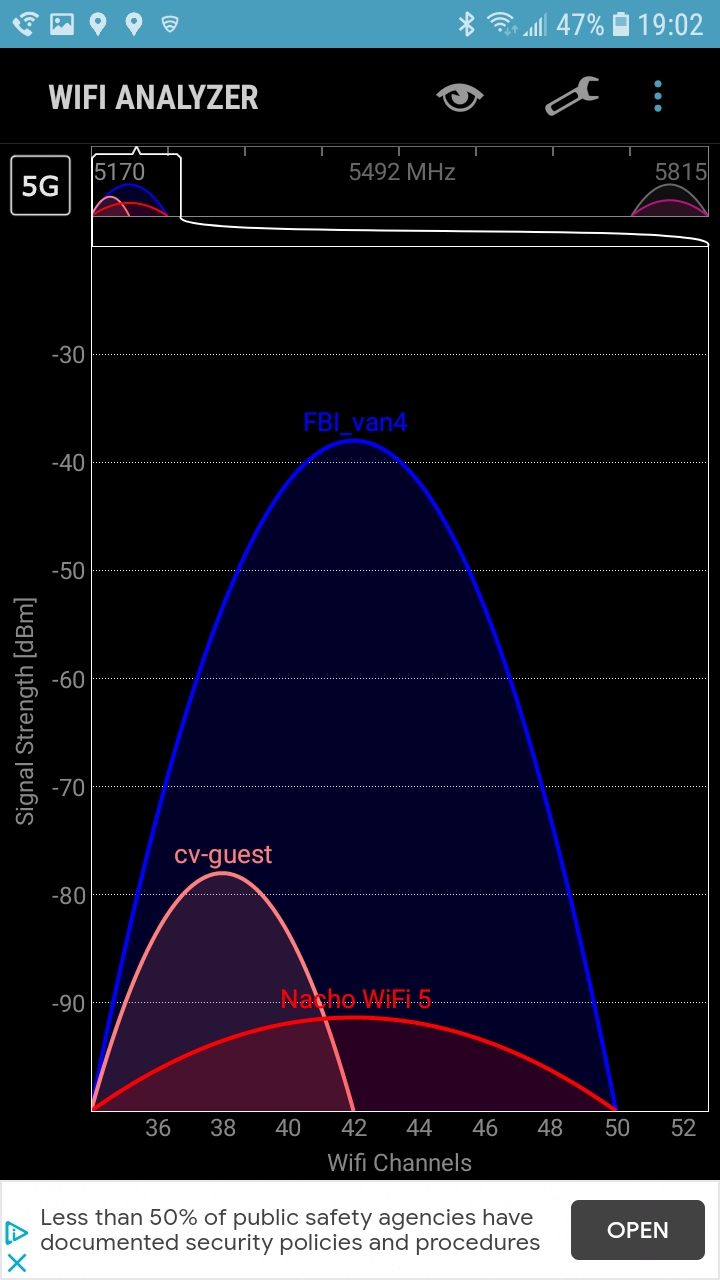
WiFi Analyzer
app for 2.4 GHz and 5 GHz.
Yes, FBI_van3 and FBI_van4
are my 2.4 and 5 GHz SSIDs, respectively.
2.4 GHz channel 1 might be a slightly better choice for me
than channel 11, at least at the moment captured below.
Above, channels 1 and 11 are about equal.
The HP-Print-37-Envy 5530 series* device
is a
multifunction printer/scanner device
like the one I bought at a thrift shop.
Wireless is turned off on mine, either that doesn't work
correctly or a very close neighbor has one.
Or, you can use the command line if you dare:
# iwlist wlo1 scanning | egrep 'Frequency|Quality|ESSID' | sed 's/Frequency:/ i ---------------------------------' | sed 's/^ *//' --------------------------------- Frequency:2.417 GHz (Channel 2) Quality=47/70 Signal level=-63 dBm ESSID:"NEKOGEAR_2.4G" --------------------------------- Frequency:2.417 GHz (Channel 2) Quality=66/70 Signal level=-44 dBm ESSID:"TP-Link_22C5" --------------------------------- Frequency:2.437 GHz (Channel 6) Quality=54/70 Signal level=-56 dBm ESSID:"DIRECT-Yd-Dell d397" --------------------------------- Frequency:2.457 GHz (Channel 10) Quality=45/70 Signal level=-65 dBm ESSID:"TP-Link_3D8E" --------------------------------- Frequency:2.462 GHz (Channel 11) Quality=34/70 Signal level=-76 dBm ESSID:"MasterPao" --------------------------------- Frequency:2.462 GHz (Channel 11) Quality=70/70 Signal level=-34 dBm ESSID:"FBI_van3" --------------------------------- Frequency:2.462 GHz (Channel 11) Quality=30/70 Signal level=-80 dBm ESSID:"\x00\x00\x00\x00\x00\x00" --------------------------------- Frequency:5.18 GHz (Channel 36) Quality=41/70 Signal level=-69 dBm ESSID:"cv" --------------------------------- Frequency:5.18 GHz (Channel 36) Quality=41/70 Signal level=-69 dBm ESSID:"cv-guest" --------------------------------- Frequency:5.22 GHz (Channel 44) Quality=70/70 Signal level=-36 dBm ESSID:"FBI_van4" --------------------------------- Frequency:5.22 GHz (Channel 44) Quality=32/70 Signal level=-78 dBm ESSID:"cv" --------------------------------- Frequency:5.22 GHz (Channel 44) Quality=29/70 Signal level=-81 dBm ESSID:"cv-guest" --------------------------------- Frequency:5.765 GHz Quality=31/70 Signal level=-79 dBm ESSID:"NEKOGEAR_5G" --------------------------------- Frequency:5.765 GHz Quality=25/70 Signal level=-85 dBm ESSID:"TP-Link_3D8E_5G" --------------------------------- Frequency:5.785 GHz Quality=55/70 Signal level=-55 dBm ESSID:"TP-Link_22C5_5G" --------------------------------- Frequency:2.412 GHz (Channel 1) Quality=38/70 Signal level=-72 dBm ESSID:"cv-guest" --------------------------------- Frequency:2.462 GHz (Channel 11) Quality=58/70 Signal level=-52 dBm ESSID:"cv" --------------------------------- Frequency:2.437 GHz (Channel 6) Quality=29/70 Signal level=-81 dBm ESSID:"The Lan Before Time 2.4" --------------------------------- Frequency:2.412 GHz (Channel 1) Quality=36/70 Signal level=-74 dBm ESSID:"cv" --------------------------------- Frequency:2.457 GHz (Channel 10) Quality=26/70 Signal level=-84 dBm ESSID:"WAVLINK-N" --------------------------------- Frequency:2.417 GHz (Channel 2) Quality=22/70 Signal level=-88 dBm ESSID:"NETGEAR73" --------------------------------- Frequency:2.437 GHz (Channel 6) Quality=22/70 Signal level=-88 dBm ESSID:"ZyXELC26F90" --------------------------------- Frequency:2.452 GHz (Channel 9) Quality=19/70 Signal level=-91 dBm ESSID:"RX_WIFI" --------------------------------- Frequency:5.2 GHz (Channel 40) Quality=20/70 Signal level=-90 dBm ESSID:"Nacho WiFi 5-guest"Wi-Fi Channel Planning Best Practices Designing a Dual-Band Wireless Network Which Wi-Fi Channels Should I Use?
For the 5 GHz band and 802.11a/h/j/n/ac/ax, in most countries there are channels 32 through 165, centered at 5160 to 5825 MHz in non-overlapping 20-MHz-wide slices. Some are 20 MHz channels, others combine two slices for 40 MHz channel width, or four slices for 80 MHz channel width. Your Wi-Fi router will likely have an "auto" choice, but who knows what it will really do. Automatically scan the 5 GHz band and make an intelligent choice? Hopefully, but not necessarily.
So what about that "telling lies" analogy?
The NAT device is lying about the internal network. It pretends that the internet network doesn't exist, and that the firewall is really everything you have inside. And remember:
Make certain that your lie is plausible. The NAT device claims that all traffic is from/to its external port, which is a routable address.
Above all, make certain that you are consistent in your lying. The NAT device keeps track of the multiple connections it is masquerading on behalf of internal hosts.
If you care about the details: It uses unique source TCP ports, thus unique client sockets, for every masqueraded connection. So yes, to be pedantic, it is doing both NAT and PAT (Port Address Translation) simultaneously.
Based on the destination port of the inbound packet, it can figure out which, if any, existing connection the packet belongs to. It can then change the TCP and IP headers accordingly before sent the packet across the interior LAN. The external socket (IP/port) maps onto an interior socket (IP/port) according to the current translation table.
But what about UDP traffic, like DNS lookups, NTP clock synchronization, or even some audio streams? While there is no connection in the TCP sense, it also does the necessary tricks with UDP ports.
How can I do this for free with a Linux machine?
Run a shell script like the following at boot time to
enable NAT.
Make sure you get this right, it really matters
where you use regular quote characters (ASCII 0x27,
typically just to the left of the <Enter> key,
at least on US keyboards)
and where you use back-quote characters (ASCII 0x60,
typically somewhere in the upper left region of the keyboard,
at least on US keyboards).
Also parenthesis (ASCII 0x28/0x29) versus curly braces
(ASCII 0x7b/0x7d).
#!/bin/bash # Turn on IP forwarding (routing) echo '1' > /proc/sys/net/ipv4/ip_forward # Figure out what the external IP address is. # This assumes that p7p1 is the external port. # Be aware of the modern network interface names. EXT_IPADDR=$( ip -4 addr show p7p1 | awk '/inet/ {print $2}' | cut -d / -f 1 ) # Turn on NAT iptables -t nat -A POSTROUTING -o p7p1 -j SNAT --to-source ${EXT_IPADDR}
The kernel maintains the "NAT table", the list of currently masqueraded connections. Put another way, it keeps track of the lies it's telling and keeps them consistent. You can view the NAT table or just see how many connections are currently being masqueraded:
conntrack -C conntrack -L
Amazon
ASIN: B00JY4QCJQ
Amazon
ASIN: B00R2AZLD2
At the SIGGRAPH Conference in Los Angeles in 2005, we used one Linux host with a 2.3 GHz CPU to do address translation for the entire conference site.
The Linux machine was handling over 9500 simultaneous network connections and its CPU was still something over 95% idle.
We did this because a $15,000 (but old) Cisco router did not have the needed performance. Cisco routers are extremely good at routing, which can be done in hardware. NAT takes processing, and routers traditionally have not had very powerful CPUs. The last I heard, the Los Angeles Conference Center was looking into Linux. And, Cisco has moved away from slower Motorola CPUs to IA64 systems, basically PC motherboards.

Linux machine running NAT at the Los Angeles Conference Center. Overworked Cisco routers in the background could not handle the load.