
Minimize the Impact of Smart Phone Loss or Theft
Loss and Theft are Always Possible
I wish I could tell you how to prevent losing your phone
or having it stolen.
But there's no way to do that.
My phone was stolen four days into
a four-week international trip.
It didn't turn into a disaster of a ruined trip
and identity theft,
because I already had things set up for reasonable security.
But, I made further changes after that episode.
Here's what worked for me,
and what further improvements I made.
Asides and further detail in
grey like this
go deeper, you might want to skip them on a first reading.
First, though, in case this is urgent:
Find and erase my Android device Find and erase my Apple device
Other Harsh Truths
In addition to your inability to prevent all loss and theft...
Increased convenience usually means decreased security. When you're offered something that promises to make things easier, carefully consider whether it increases your risk. Be skeptical. Does an offer benefit you? Or the business?
Increased confidentiality (or privacy, or secrecy) usually means decreased availability (or reliability, or usefulness). Let's say you turn on multi-factor authentication for some online account, requiring you to enter a randomly generated number received via text message. If you don't have your phone, you are now locked out of that account. I try to set things up so I will have my choice of text or email for MFA, but many businesses only support text.
More on these issues appears in following sections.
Device Authentication is Your First Line of Defense
When you turn on or reboot your phone, it should require authentication. You, or whoever has your phone, should have to enter an 8-digit PIN and possibly scan your fingerprint, ideally both, before you can do anything. And please, no trivial nonsense like 11111111 or 77777777 or 12345678. If this seems too difficult, why not the last 4 digits of your phone number and then your bank PIN? The person who steals or finds your phone won't know who you are, or what your phone number is.
4-digit PINs are weaker than you would expect. An excellent analysis studied a collection of almost 3.4 million user-selected four-digit PINs and found that:
-
Nearly 11% were
1234, over 6% were1111, and nearly 2% were0000. -
If you try guessing just the top 5 most popular you
will get over 20%:
1234at 10.713%,1111at 6.016%,0000at 1.881%,1212at 1.197%, and7777at 0.745% add up to 20.552% out of all 10,000 possible 4-digit PINs in the collection. -
Many are effectively just two-digit PINs.
Repeated couplets such as
7878or1414account for 17.8% of the collection. -
Many people use memorable years,
or dates such as birthdays in
MMDDorDDMMformat, or life events inMMYY. Those formats greatly constrain the set of possible choices. -
Numerical runs like
2345and9876are very popular, as is the straight-line keypad sequence2580. -
Even numbers are a little more popular, so
2468is used more often than1357.
When the screen blanks after a short period of inactivity, or when you blank the screen with a button press, you should have to do another fingerprint scan to unlock it.
Which is stronger, fingerprint or face recognition? I don't see a strong advantage to either. You can find analyses arguing both ways. I think it really has to do with the specific algorithms used by your carrier's customization of Android or iOS. Either one is a vast improvement on no biometrics at all.
Drawing a pattern on the screen is, by far, the weakest form of authentication. Don't do that. Learn how to enter a PIN.
Keep Especially Sensitive Information and Activity Off Your Phone
Do not install apps from your bank or other financial institutions.
These institutions constantly encourage people to install their smartphone app so you can check your balance on the go.
If you feel that you need to check your bank balance, or your credit card charges, or your credit score, or your car or health insurance, or other financial measures every single day, then you probably have some serious financial problems. Unless, of course, it's a psychological issue in which your obsessive behavior is getting out of control. Either way, you shouldn't be out wandering around in public. Go home or to work and get your finances in order. Or consult a psychiatrist if needed.
Deal with the underlying problem. Don't install financial apps.
Besides, I suspect that the business, or more catastrophically, the contractor who wrote the app, wants to harvest all your personal information. And/or mine bitcoin.
Own a Desktop or Laptop Computer and Limit Financially Sensitive Activity to That
That's the extent of this tip — Keep all financial information off the electronic device that's most likely to be lost or stolen. Handle your sensitive data only in a somewhat secure location. Not on the cross-town bus.
Advanced topic — Consider encrypting the file system on your laptop. That will be far easier to accomplish when you buy a new one, or if you re-install the entire operating system as Linux and BSD users do from time to time. I put this on my to-do list for the next major release of Linux Mint, my preferred desktop and laptop distribution.
The Same for Sensitive Email
Most of us have an email account that is the key to all of our online identities. For example, to sign in to your bank's web site, you must enter your username and password, and then also enter a six-digit number emailed to this account. Do not access that email account on your phone. Only access it on your bulky, less-portable, and less likely to be lost or stolen, laptop or desktop.
"But I want to use email on my phone!"
Fine, keep in touch with family and friends with a second, non-critical, email address. Just don't do any sensitive email with it, nothing financial or medical. Not for the second-factor authentication emails.
Know That Remote Tracking and Remote Wipe Are Available
Both Android and iPhone provide ways to sign into your account on another device, locate your phone (or at least where the network last thought it was), and remotely erase the data. Unfortunately, there is no "Remote Detonate" option, but at least "Remote Erase" works.
Notice that you need to sign into the OS manufacturer,
google.com or apple.com,
and not your service provider.
Find my Android device Find my Apple device
Advanced topic — it's commonly called "remote wipe" but it doesn't really wipe out the data. It deletes the references to the data files, but it does not overwrite the actual data. For example, if you have pictures stored on a micro SD card within the phone, after a "remote wipe" you still could pull out the memory card and recover all the images with recoverjpeg or a similar tool.
Even more advanced, to the point of pedantry — what it really does is mark those data blocks as free, currently unused and available, within the file system data structure. Existing sensitive content remains in the data blocks.
Use a Password Manager, and Use it for More Than Just Passwords
A web-based password service in which you store your passwords in someone's distant web server is a hilariously bad choice. Use a local password manager.
I use KeePass, which is available for many platforms. There are others, I will explain and show what I use.
Like other quality password managers, KeePass lets me organize records into categories and sub-categories. It has a search function for when I forget the exact name I used for an identity.
KeePass uses strong cryptography. The overall security will be limited by the complexity of your master passphrase. To support the full cryptographic security of AES-256 and SHA-256, you would have to use a long and complex passphrase that would be very difficult to enter correctly when you can't see what you're entering. Worry about the complexity of your master passphrase, don't worry about internal algorithms.
For each individual identity, KeePass shows you its passphrase's length in characters and an estimate of its strength in bits.
Each entry has an associated free-form text "Notes" area. Use that to store further information — account number, contact information, and so on. For a credit card, that can include expiration date and CCV, the three-digit code on the back. An entry doesn't have to be an identity, the user name and password fields can be empty. For example, I have one named "Credit Cards" with neither user name nor password, it exists to hold a "Notes" field with a list of entries of issuer, card number, expiration, CCV, and issuer contact information.

In the days of landline phones,
you typically could make free calls only to nearby numbers.
Maybe half of the county where you lived,
which for me meant half of
a roughly 20×20-mile area.
Beyond that, the phone company billed you per minute.
If you called between 11 PM and 7 or 8 AM,
or over the weekend,
it was cheaper but you still had to pay by the minute.
Starting in the mid to late 1980s,
you could get a calling card
with which you first called a toll-free number,
then entered your calling card number,
and then the phone number you wanted to call.
By the late 1980s, "dime a minute",
or US$ 0.10 every 60 seconds,
was heavily marketed as a remarkably cheap rate.
Now I can make
unlimited
free calls within the U.S.
(once, of course, I have paid the monthly charge,
but considering inflation that costs about what
a landline cost in the 1980s).
With my T-Mobile contract,
I can even call back to the U.S. from overseas for that
US$ 0.10/minute rate that used to be considered cheap
for a 10-mile call.
If you're from the U.S. or Canada, companies still emphasize their "toll-free" telephone number. For most of us, toll-free numbers are historical relics. The big problem is, you cannot call them from overseas. Store the alternative plain old phone numbers for all financial accounts, your mobile phone provider, plus anyone else you might need to contact in an emergency.
After my phone was stolen during a brief stopover in Paris, it took me a while to find a non-toll-free number to contact T-Mobile customer support. Then I had to find a way to call that number.
By that point, I was in Casablanca, Morocco, staying in a hotel with direct-dial phones in the room but they couldn't call outside the country. "Phone centers", businesses with a bunch of little booths where you can place overseas calls and then pay at the counter, were still pretty common in the 2000s. But the people at the hotel's front desk didn't know of any still operating nearby in late 2023. One staff member said that maybe I could use his mobile phone. He estimated that the call would cost about 10 dirham per minute, not quite US$ 1. Yes, please, and I gave him almost twice that for the 13-minute call, a fistful of dirham as well-deserved baksheesh.
When I got customer support on the line and said that my phone had been stolen, I was immediately connected to someone who handles those cases all day long.
She asked where I was, and I said Casablanca, Morocco. She immediately told me that if we got disconnected, call back — to a toll-free number that I couldn't reach from overseas.
I reminded her that I was using a borrowed phone, and the whole point of my call was that I no longer had my phone. And, toll-free numbers are not reachable from outside the U.S.
Then she kept suggesting that I visit one of their stores for immediate assistance. I explained to her that I had considered that, and discovered that even though T-Mobile is a subsidiary of a German company, the closest T-Mobile store seemed to be in the state of Maine, clear across the Atlantic.
Well, she asked, how in the world was I going to proceed? I explained that I had done the remote erase, and I hoped that she could disable the phone. Yes, she could, and see the details about that in the next section.
"But, but... What are you going to do?", she asked, apparently more out of morbid curiosity than planning her next suggestion.
I had another three and a half weeks on my trip. I'm sure I would be somewhat inconvenienced, but I would deal with it.
"HOW CAN YOU POSSIBLY DO THAT?", she almost screamed.
I lived through it. I had a fairly low-end digital camera, so I could take pictures. I had been in Morocco just a year before, and to Turkey several times, Syria twice, and Egypt once, and I was quite certain that the souq in Marrakech, my next destination, could easily provide me with a battery-powered alarm clock. Yes, a wonderful Aladdin's cave of a hardware shop a 50-meter stroll from my lodging in the Marrakech medina had one complete with battery for the equivalent of about US$ 1.50.
Flustered, she again urged me to immediately visit a T-Mobile shop. I reminded her that the nearest one was across an ocean. I would go to one early in the morning after flying back into Chicago, three and a half weeks into what she saw as my grim future.
I verified that the phone was disabled world-wide, she again urged me to try to call unreachable toll-free numbers from overseas, and we ended the call.
I got back, I'm writing this a few months later.
I had arranged all my lodging in advance through
Booking.com,
and had saved PDF versions of my reservations on my laptop,
which I could haul out and start up,
and I had also printed them out.
Toner on paper is more reliable than small
electronic devices.
The tricky part would be finding my lodging
at a couple of upcoming stops as I moved about
Morocco by train.
Online research with my laptop on Google Maps the night before,
a hand-drawn map on the back of that printed reservation,
and the problem was solved.
Include All Utilities in Addition to Mobile Phone Provider in the Password Manager
Especially your mobile phone provider, because we're thinking about the loss or theft of the phone. I can't imagine why I would urgently need to contact my electricity provider when I'm out of town. But I do also include records for the water, sewage, gas, and all other utility providers, and now I have them all in one place.
However... A copy of a utility bill, especially multiple ones, is often accepted as proof of identity. If you itemize deductions on your taxes, you need to keep copies of pretty much everything, including utility bills. I do consulting work from a certain percentage of the area of my home, meaning that the same percentage of my utilities and insurance count as business expenses. The good news is that PDF files of utility bills are easy to keep, no more bulky paper files that I need to retain for seven years and then find a safe way to destroy them. The bad news is that each utility is yet another identity I must protect so I can safely log in to the electric company's web site and download the monthly statements.
Make sure to include your account number and the IMEI number for your phone. When you contact your provider to report a lost or stolen phone, they can look up both of those based on your phone number. However, the T-Mobile representative told me that I had significantly accelerated the process by having them ready when I contacted her.
The SIM card is associated with the provider and the phone number. The IMEI number is sort of a chassis ID for the phone itself, staying with the phone when the SIM is replaced.
That is, for most providers world-wide.
Some U.S. providers use CEIR, but not all.
At least T-Mobile does that.
The U.S. government doesn't require it,
because there's no way for the phone companies to monetize it
and they cry about participation imposing financial hardship.
For them, not you, they don't care about you.
The Saudi Arabian government uses IMEI tracking to
locate and apprehend women who are fleeing abusive owners.
Male relatives.
Whatever.
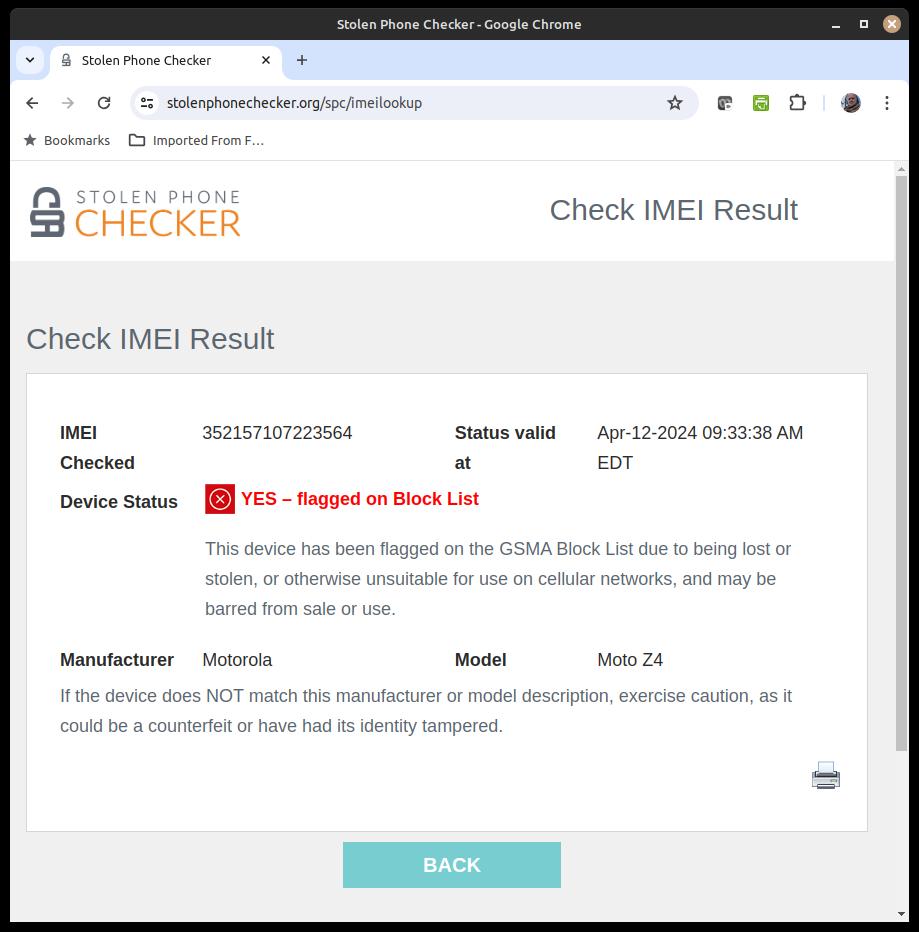
Given the IMEI number, the provider can immediately block its use on their network. Better yet, they can submit it to the CEIR, a central registry used by providers, meaning that the lost phone is unusable world-wide.
You can find the IMEI number by going into the Settings menu
and selecting something like "About Phone".
You might be able to access the IMEI number
by entering *#06# on the keypad.
You can query the CEIR registry at sites like stolenphonechecker.org, where I got this screen shot:
Have a Primary and Secondary Browser
Ages ago when buying my first smart phone I opted for Android over Apple. That means that when I sign into my Google account, something that happens when I first unlock my phone after a reboot, or when I first start the Chrome browser on my laptop or desktop, that session has access to all my Chrome settings. If I have Internet access at the time, they aren't really just stored in the local browser data storage area, they are stored out in the Google cloud. For iPhone owners, it's the same thing but Apple. (What if you use Chrome on an iPhone? I don't know...)
On Linux/BSD, I think
that my Google credentials are stored in:
.config/google-chrome/Default/Login Data For Account
which ls and file tell me is a
54-kbyte SQLite 3.x database file.
Or, possibly
.config/google-chrome/Default/Login Data
which is a roughly 400-kbyte SQLite 3.x database file,
but I think the second one stores what you see as the
Password Manager within Chrome, for websites.
The benefit is that all my bookmarks and browsing history are mirrored, live, across my devices.
The danger is that all saved logins and passwords are also mirrored through my Google account. It's that convenience-versus-security trade-off again.
That also worked well for me initially because I felt that Chrome's Developer Tools were superior. Those in Firefox are at least as good now, but not strikingly better.
For me, Chrome is my browser with the primary security concern. I can use Firefox for random web page viewing, and to test cross-browser compatibility of web page design.
Don't allow any browser to save your login and password for any sensitive account. Loss of one device could expose it across all platforms.
Yes, that means that if I want to check my bank balance, I need to start my password manager and copy-paste two fields. But why would I really need to suddenly check my bank balance? It's not as if I'm walking down the street and think "Huh, maybe I should buy a car right now." Financial institutions will try to convince you to install their apps. Don't do that.
If you think "Maybe I should get dinner at a restaurant, if I can afford it", then you can't. You should be at home eating a can of beans. Supermarket house-brand beans, not the fancy stuff.

I only very grudgingly use web mail. No, I use web browsers for browsing web pages, and Thunderbird, a dedicated email tool, for email. I keep the message view in Plain Text mode, except for the organizations who send email that you can't accurately read, or read at all, switching to HTML mode for that one message.
It's surprising, or maybe not, how many organizations that think of themselves as super professional send out emails that contain irrelevant nonsense when you view them in Plain Text mode, with their content hidden away in the HTML version. For example, both Google Webmaster Tools and Microsoft's Bing Webmaster Tools.
If I want to view a web page recommended in an email, I right-click and copy the URL in Thunderbird, then go to a browser window, open yet another tab, and paste it into there. That started as a habit that I got into, but it's another thin but non-zero barrier between web pages and my email identity.
This behavior caused a friend to call me a "Post-Modern Luddite", a title I'm thinking of putting on my next batch of business cards.
Which Browser is More Secure?
Have you noticed that I haven't even mentioned Microsoft's browsers? Explorer had actually become pretty good, but then they abandoned that for Edge.
I don't think there's really any significant difference between Chrome and Firefox.
Use whichever browser(s) you prefer, keeping in mind the Android–Chrome–Google and the iPhone–Safari–Apple connections.
A lot of people get really wound up over Google, and Internet advertising in general, tracking you. I don't have the energy to maintain that level of outrage over something that I, unfortunately, really can't control.
I have found, and notably during my Great Phone Debacle,
that it can be very useful to have a second browser.
I would have to fight with Chrome to do very much in it
without signing in to my Google account.
But I could simultaneously use Firefox to do things
at Google, including android.com
and gmail.com,
without a struggle.
Whichever browsers you use, have them not store passwords, except for truly trivial accounts.
It's useful to have multiple email identities,
at different providers.
I have a gmail.com address that auto-forwards
to my primary comcast.net email identity.
But I also have a second gmail.com address
that does not auto-forward.
If I have my phone,
the very infrequent messages to that account show up there.
When my phone was stolen,
I could (grudgingly) use the
gmail.com web interface
to send and receive with that account.
Again, that was very helpful a few times.
Some email providers may be rather fussy about
your mobile endpoint.
If, for example, you're staying at a low-cost place
in the medina in Marrakech, or Tangier.
The provider may do so in a way that
Thunderbird pops up a notice
that your email client is at an IP address
on the current spamhaus.com block list.
An email account hosted at outlook.office.com,
which I only use for the consulting work,
is an example of that behavior.
Or, it may fail silently,
meaning that the server won't establish a TCP connection,
silently dropping your connect attempts.
That's what I have experienced with my Comcast account,
for which mail.comcast.net is actually
imap.ge.xfinity.com.
Capturing packets in a terminal window with:
$ sudo tcpdump -i any -vvv tcp port 995
can reveal that an explanation is inserted in the
rejected TCP handshake, which Thunderbird doesn't show.
Synchronizing Password Manager Databases
When I'm getting things done at home, I'm sitting at my desktop. Email is Thunderbird running on my laptop but displaying on the desktop, because I started it by typing this on the desktop:
$ ssh -fXC laptop thunderbird
If I want to sit on the couch and use computers, I carry the laptop from the second desk over to the couch.
If I'm preparing to leave on a trip, I make sure that my laptop has the latest version of my KeePass database. That's a good time to make sure that the one on my phone is also up to date.
I use the
mtp-tools
package, and specifically the aft-mtp-mount
command.
Connect the phone via USB,
kill a GNOME process that otherwise would be fighting
unsuccessfully for control,
and run a command:
$ pkill gvfs $ mkdir /tmp/phone $ aft-mtp-mount /tmp/phone
Then poke "Allow" on the phone screen as it asks if the USB access is OK.
The password database on my laptop and desktop is in:
~/.keepass2/keepass.kdbx
But where is it on my phone?
Let's find out:
On Android, as customized by T-Mobile for Samsung phones,
it's in:
$ find /tmp/phone -type f -name keepass\* /tmp/phone/Internal\ storage/Android/data/keepass2android.keepass2android/files/keepass.kdbx
Or at least that's where it ends up on Android as customized by T-Mobile for Samsung phones. Let's set a variable to make things a little less tedious:
$ dir=/tmp/phone/Internal\ storage/Android/data/keepass2android.keepass2android/files
Now, which is newer, the one on the computer,
the one on the other computer,
or the one on the phone?
Let's say I'm doing this on my desktop,
and laptop is the name of my laptop.
I'll ask about the local file and
the file on the connected phone;
see what the file on the phone seems to be,
and then ask the laptop about the file over there:
$ ls -l .keepass2/keepass.kdbx $dir/keepass.kdbx -rw------- 1 bob bob 45166 Mar 30 11:24 .keepass2/keepass.kdbx -rw-r--r-- 0 root root 44878 Feb 25 16:19 /tmp/phone/.../keepass.kdbx $ file $dir/keepass.kdbx /tmp/phone/.../keepass.kdbx: Keepass password database 2.x KDBX $ ssh laptop ls -l .keepass2/keepass.kdbx $dir/keepass.kdbx -rw------- 1 bob bob 45166 Mar 30 11:24 .keepass2/keepass.kdbx
Yes, owner, group, and link count aren't what you would expect, because of some weirdness with how MTP works.
It looks like the desktop and laptop are in sync,
while the one on the phone
(currently connected under /tmp/phone/)
is a little over a month behind.
It's definitely different, notice the smaller size,
and it's older according to the timestamps.
To be extra cautious, I could verify that the contents are identical on the desktop and laptop:
$ openssl sha256 .keepass2/keepass.kdbx $dir/keepass.kdbx SHA256(.keepass2/keepass.kdbx)= 029c44bad3c6c0983e27abcc2148e187053c4dd1cd40ea8b6edfdebd6f298064 SHA256(/tmp/phone/.../keepass.kdbx)= f95816cd87fb242b894efb45d3bdae76b912f843d06e9239bbc084c05e558f5e $ ssh laptop openssl sha256 .keepass2/keepass.kdbx $dir/keepass.kdbx SHA256(.keepass2/keepass.kdbx)= 029c44bad3c6c0983e27abcc2148e187053c4dd1cd40ea8b6edfdebd6f298064
Yes, notice that the local files on both computers
have identical hashes,
and so, beyond any reasonable doubt, identical contents.
It's safe to proceed.
The -a means "archive mode",
preserving timestamps.
Or maybe you prefer
rsync
for this.
$ cp -a .keepass2/keepass.kdbx $dir/
When I return from a trip, I need to re-synchronize things.
Unfortunately,
there's no way to do a three-way comparison between databases,
the way you could use the
diff3
command on three text files.
There's some good news, though. When you open an entry in KeePass, you will see a History tab. If you overwrite a database and need to roll back to earlier versions, that will be available. But be very careful, that would be tedious and you would very much prefer to avoid that problem!
Other Financial Pieces
I have everything set up for autopay. Sometimes two levels — monthly health insurance is automatically charged to a credit card, and the credit cards are automatically paid from my checking account.
So, if I'm going to take off on a three to four week trip, I need to make sure I have enough in that account. Maybe around week 2.5 or 3.5 I'll sign in to the credit union on my laptop and make sure things look OK.
I carry four cards, planning to use them in various ways:
- US Bank VISA card — No fee on overseas purchases, but an expensive way to get cash overseas.
- CapitalOne MasterCard — No fee on overseas purchases, but an expensive way to get cash overseas. As a MasterCard, it provides the collision and damage coverage that car rental companies always want you to purchase at very high rates, so I make sure to rent a car with this one!
- CitiBank debit card — Minimum charges for getting cash from bank machines world-wide. Every convenience store in Japan has an ATM from which I can withdraw almost-no-fee Yen, and there's usually a convenience store no further away than you could throw a Pokemon.
- Purdue Federal Credit Union debit card — If I can find a credit union in the U.S., I can get cash with no fee. Otherwise, this one is just a backup.
But, but... What about the megathrust earthquake when the Cascadia Subduction Zone comes loose? Yeah, and what if a comet hits the Earth?
Then, if one is lost or disabled because of a breach,
I have the others as backups with slight financial penalties.
And, remember, details on all are in KeePass on my phone,
my laptop, and a copy stashed at
cromwell-intl.com in
~/.keepass2/keepass.kdbx.
That's in a Google data center somewhere along the
Columbia River.
Unfortunately, there doesn't seem to be a way to dump an
entire KeePass database into a text file,
print that, and keep it in the fireproof box at home.
Full Disclosure
I do have two business apps on my phone — Starbucks and Einstein Brothers Bagels. Both have my credit card info stored on their server, and while I can delete a card and add a new card, I can't see the current card info, neither could a thief. Both provide free coffee (every advance order at Einsteins, occasionally in person at Starbucks), and I see it as a reasonable trade-off.
The Aftermath
The phone-free three and a half weeks was somewhat of a cleansing experience. Despite T-Mobile's alarm, I survived.
My first morning back in Chicago, I walked to a nearby T-Mobile store and bought a new phone. I already had been planning to do that. I said that I wanted one with in-display fingerprint reader and support for 8-digit PINs, and they said that pretty much all Samsung models have those.
I retained my existing phone number, which saved quite a bit of hassle.
All the pictures I had taken with the stolen phone, except two or three in the evening before the next morning's theft, had been automatically backed up to my Google account.
I Hope You Never Need This
But if you do, I hope this helped!
Throughout this page I will use "financial institution" to mean banks and credit unions, investment firms and advisors, and any other organizations and people who hold or can access your money.